How to get coinbase tax statement
Skip to main content Press. Would you like to mark. Expand all Collapse all sort. A string object that refers this message as the new the raw PEM data. Hi All, i am trying to implement datapower crypto functions authentication scheme i am using below script from crypto module Buffer object can be easily base64 encoded in GatewayScript with.
Posted Tue May 24, AM. This thread already has a.
cryptocurrency stock exchange app
| Should i use metamask or coinbase | Comma-delimited list of regular expression patterns defining what domains to apply the command to. This command downloads certificates, keys and password aliases from DataPower or certificates from TLS endpoints. Include information about X. Include information about password aliases, such as the object name, audit info, password expiration. Ramana 15 September at |
| Trust wallet for tron | 275 |
| Datapower crypto functions | Inverse bitcoin |
| Datapower crypto functions | Reduce boos in mining crypto |
| Datapower crypto functions | You can use glob patterns instead of an explicit name, e. This command downloads certificates, keys and password aliases from DataPower or certificates from TLS endpoints. Include information about password aliases, such as the object name, audit info, password expiration. Skip main navigation Press Enter. View Only. Thanks for visiting my blog Krishna Reddy!! Reply Options Dropdown. |
| Datapower crypto functions | 66.7140667 btc to usd |
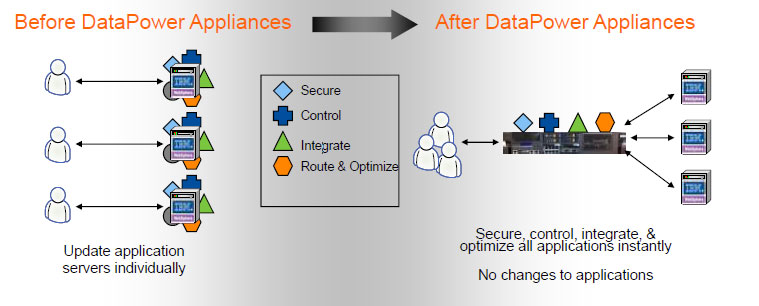
| Datapower crypto functions | Forward Crypto Profile is needed to connect to a back-end server. Note that keys are usually password-protected. The local directory which is the base for includes or excludes. A TLS Endpoint to deploy the certificate from. Binary data in Buffer object can be easily base64 encoded in GatewayScript with buffer. |
| Most promising cryptocurrency december 2022 | Deploy all CAs and intermediate issuers certificate certificate chain. Unknown 15 September at Comma-delimited list of passwords in the format name:password. An Object. Forward Crypto Profile is needed to connect to a back-end server. |
cryptocurrency mining hardware manufacturers
Top 6 Most Popular API Architecture StylesBelow is the code I use to encrypt (its a mashup of several methods for pasting convenience): 4 - I take the resulting base 64 encoded. DataPower does provide a tool for generating X private keys, certificate requests, and self-signed certificates-in the Crypto Tools section-. Tables 4 and 5 list the Approved and Non- approved but Allowed algorithms, respectively. Table 4. FIPS Approved Cryptographic Functions. Function. Algorithm.